DNSSEC adds an authentication layer to an otherwise insecure DNS infrastructure. It guarantees that visitors are directed to your serve IP when they type your domain into a web browser, thus avoiding man-in-the-middle attacks and other types manipulations during the resolution.
Do you support and implement DNSSEC?
Sellcloud supports DNSSEC for all DNS products we offer through our DNS partner ClouDNS which is a leading provider of global Managed DNS services. With 34 Anycast DNS Data Centers on six continents for optimal speed and security.
What is DNSSEC?
DNSSEC is a feature of the Domain Name System (DNS) that authenticates responses to domain name lookups. It prevents attackers from manipulating or poisoning the responses to DNS requests. DNS technology was not designed with security in mind. One example of an attack on DNS infrastructure is DNS spoofing. In which case an attacker hijacks a DNS resolver's cache, causing users who visit a website to receive an incorrect IP address and view the attacker's malicious site instead of the one they intended.
How does DNSSEC work?
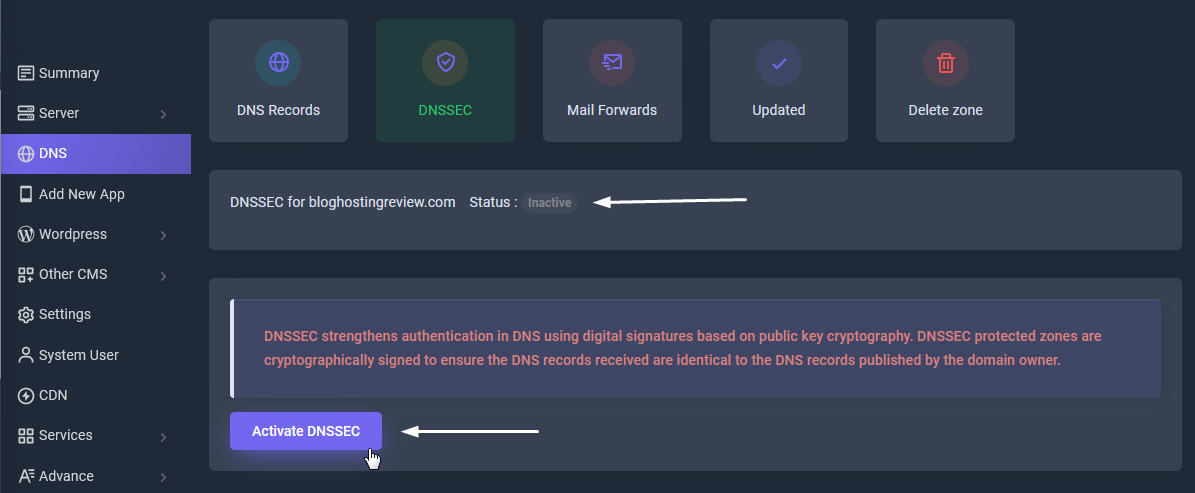
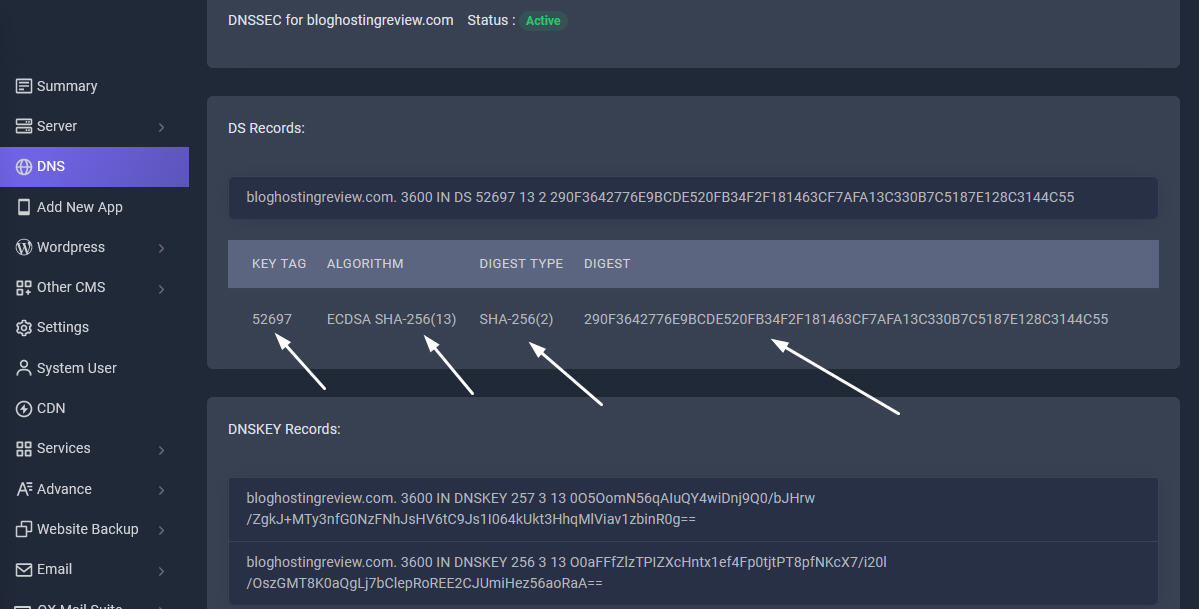
When you activate DNSSEC, we will generate a public and private key for your zone. The public key is provided to you in the form of DS or DNSKEY records. The records should be configured at the domain registrar provider, where the domain name is registered. During the deployment of your zone in our network, we will use the private key to sign all your records. These signatures will be received and checked by the end-user resolver if they match with the public keys and the resolver will be able to authenticate that the records are not manipulated during the network transfer.
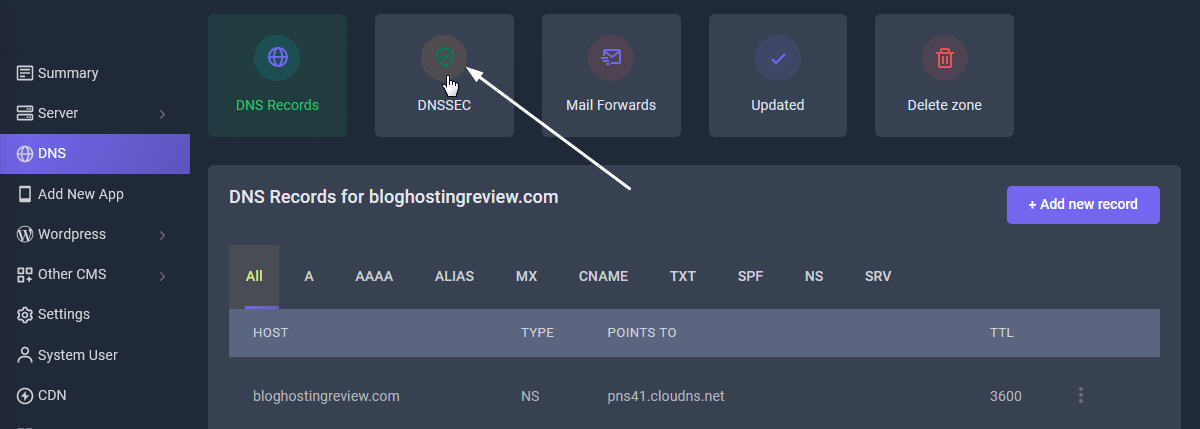
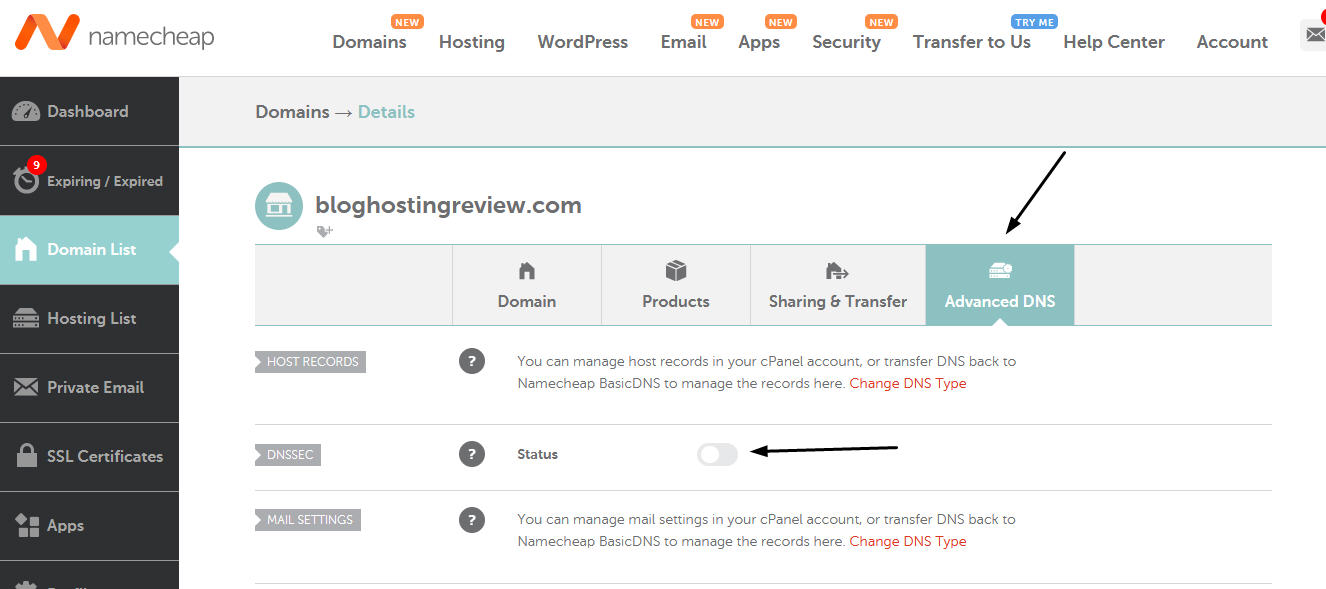
To activate DNSSEC signing and obtain the domain DS records, you have to log into your control panel and to navigate to the DNS tab zone and click your domain zone. In the zone's control panel you will see a menu in top called "DNSSEC". From this page you can activate or deactivate DNSSEC zone signing and to receive the DS and DNSKEY public records.
Encryption Algorithm
Encryption Algorithm used by the ClouDNS system to sign the zones is 13 - Elliptical Curve Algorithm (ECDSA P-256). This algorithm is considered both as strong and fast compared to the standard RSA keys, which makes your domain name both fast and secure.
Exception: Due to TLD limitations we are unable to use ECDSA P-256 SHA256 for .GDN domain names. For this TLD the default algorithm is set to RSA SHA512.
NSEC3 Records (Next Secure)
NSEC records links to the next record name in the zone (in DNSSEC sorting order) and lists the record types that exist for the record's name.
ClouDNS implements by default NSEC3 records. NSEC3 records have the same functionality as NSEC-records, except NSEC3 uses cryptographically hashed record names to prevent enumeration of the record names in a zone.
DS records setup
Once the DNSSEC is enabled in the dns zone, the DS records should be configured at the domain provider, where the domain name is registered. Most of the domain providers, including ClouDNS, and TLDs currently support DNSSEC. However, there is still limitation for some of the TLDs or domain provider's control panels. If you do not see an option to configure the DS records in the domain name control panel, please contact the technical support of the domain provider to do it for you manually, usually this is a working solution for most of our customers.
Some of the TLDs requires DNSKEY records along with the DS records in order to configure your domain name DNSSEC configuration. You can obtain the DNSKEY records from the DNSSEC page in your zone control panel.
RRSIG validity time
During the signing process of the zone the backend system generates signatures for the all records which are stored within RRSIG records within the zone. These records are stored on our dns servers and included in the zone transfers if you use secondary dns with your own server or external backup provider.
RRSIG records helps to the resolvers to validate responses received from the authority servers if they are not modified during the transfer. RRSIG records has validity period and once this period expires they become invalid and the zone should be resigned. Our system sign the zones with 30 days validity period of the signatures. After every change made within the zone we are resigning the zone and RRSIG records are signed for another 30 days validity period. If for the recent 20 days there are no changes in the zone, the system automatically resign the zone keep the signatures valid.
Keys rollover
At this moment ClouDNS doesn't implement keys rollover and there is no option to reset your keys. If you want to have new keys for your zone, you have to recreate the zone or to contact our technical support to do the change for you.
How to activate DNSSEC on your domain
To activate DNSSEC signing and obtain the domain DS records, you have to log into your Sellcloud control panel and to navigate to the DNS tab zone and click your domain zone. In the zone's domain page, you will see a menu in top called "DNSSEC". From this page you can activate or deactivate DNSSEC zone signing and to receive the DS and DNSKEY public records.
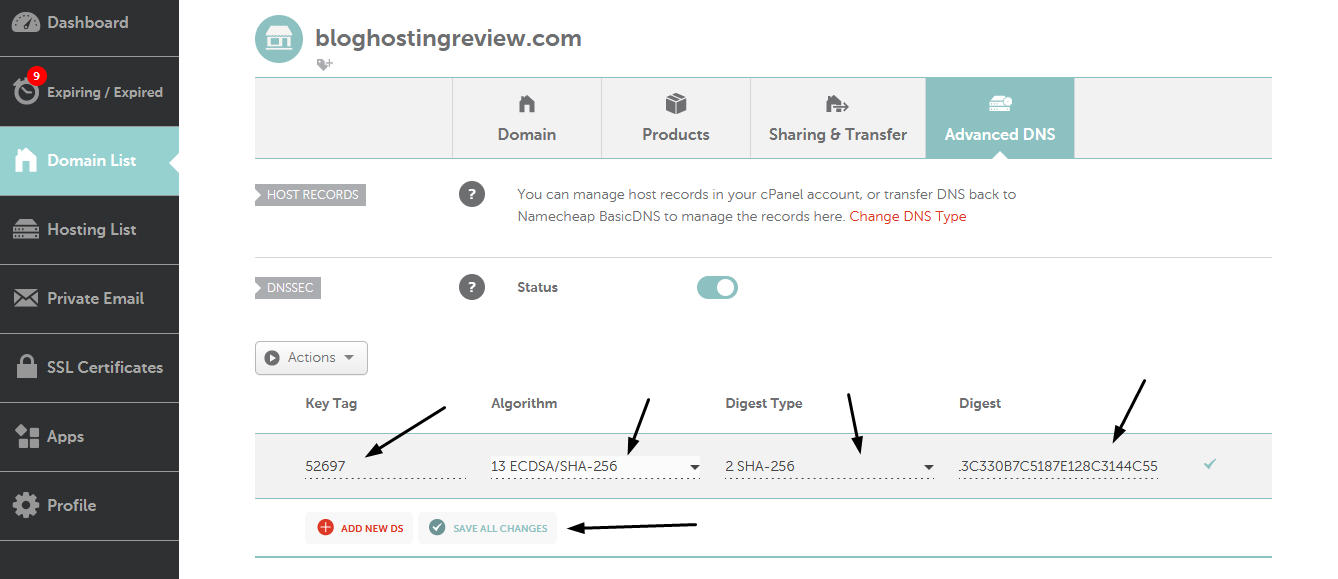
Activate the DNSSEC button in your domain registrar panel. Copy and paste the DS record consists of four fields: KeyTag, Algorithm, DigestType and Digest into the fields of the DNSSEC section in your domain registrar. After pasting, click save button. You have successfully activated DNSSEC for your domain. That's it! Now please wait 30 minutes for the settings to take effect. You can check if the changes are accepted by analyzing your domain using VeriSignc Analyzer